因为这个app(v26.2)没有内置acme 的中间证书,所以服务器端需要配置成使用fullchain.cer,
否则mobile app 的url测试失败。
因为这个app(v26.2)没有内置acme 的中间证书,所以服务器端需要配置成使用fullchain.cer,
否则mobile app 的url测试失败。
有两个piwigo插件可用户维护工作:
检查系统文件:插件和主题的完整性
可据此,安装必须的插件或主题
检查上传用户文件,与数据库是否保持一致
可删除问题文件
Acme.sh issue SSL certificate with Google
sudo su
source ~/env.sh
env|grep proxy|grep http
curl https://get.acme.sh|sh
exit
sudo su
source ~/env.sh
source /root/.acme.sh/acme.sh.env
acme.sh --set-default-ca --server google# Must install Google Cloud SDK first
gcloud publicca external-account-keys createacme.sh --register-account -m admin@zhenglei.net --server google --eab-kid "your KeyId" --eab-hmac-key "your b64MacKey"sudo su
# Stop services listen 80/443 port
#/opt/local/etc/init.d/openresty stop
source ~/env.sh
source /root/.acme.sh/acme.sh.env
# Only have IP v6 public Address
acme.sh --issue -d blog.zhenglei.net --standalone --listen-v6sudo su
source ~/proxy.sh
env|grep proxy|grep http
apt-get update
apt-get install apt-transport-https ca-certificates gnupg curl socat
curl https://packages.cloud.google.com/apt/doc/apt-key.gpg | gpg --dearmor -o /usr/share/keyrings/cloud.google.gpg
echo "deb [signed-by=/usr/share/keyrings/cloud.google.gpg] https://packages.cloud.google.com/apt cloud-sdk main" | tee -a /etc/apt/sources.list.d/google-cloud-sdk.list
apt-get update
apt install google-cloud-cli
gcloud init昨日从微信打开blog.zhenglei.net网站,出现了不信任提示
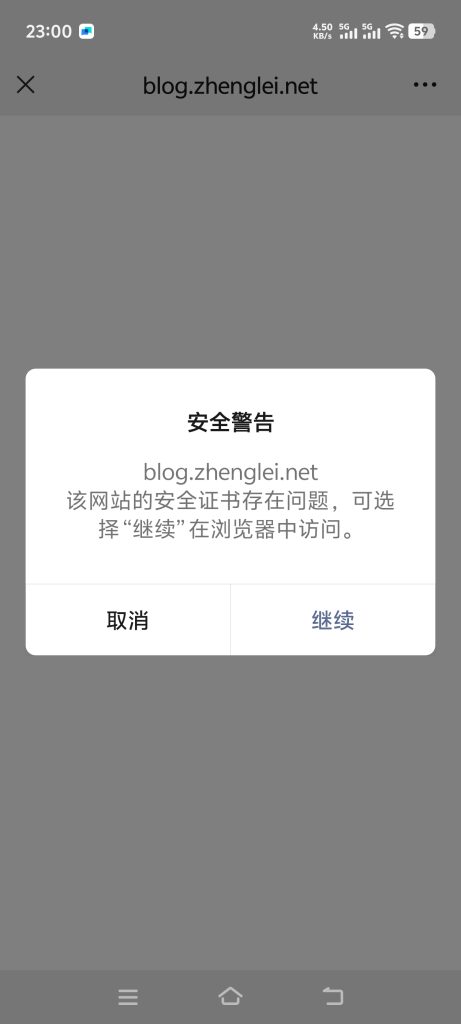
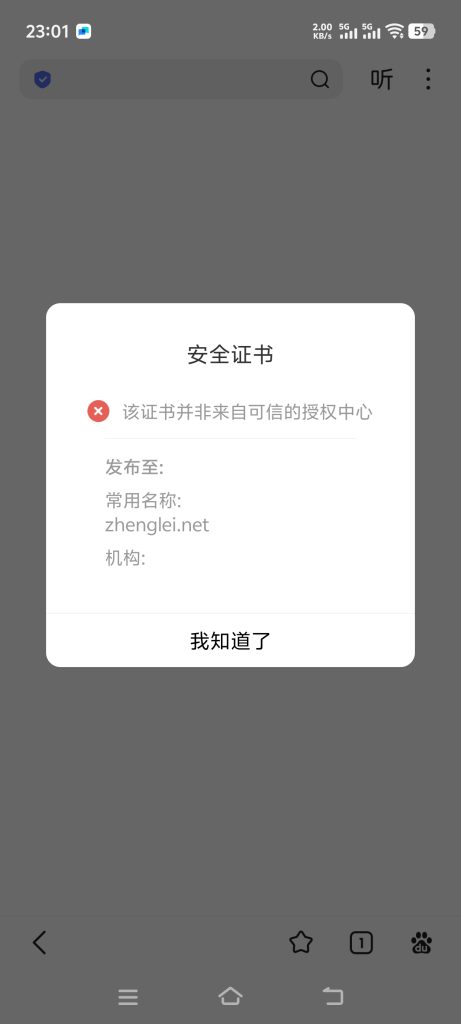
仔细用各个浏览器测试,发现的问题是:
最近在blog中直接使用了一些gallery.zhenglei.net中的图片,而因为偷懒,gallery没有配置证书,用的是http模式。
将gallery也配置成https模式后,浏览器直接打开,没有问题了。
但微信打开依然存在问题。
对我而言,微信打开有问题是个好事,说明微信对blog.zhenglei.net信任度增加了,开始使用微信内置浏览器来处理了。
微信对于外部网站,有自己的信任规则,经常变化的规则。
完全不信任的,提出警告
其次,不显示图标,用外部浏然器。
再其次,显示图标,用外部浏然器
最后是,显示图标,用内部浏然器
然而,证书哪个方面有问题,不得而知。
只好,借助于百度和谷歌,全网搜索了
有篇文章谈到了,微信的证书要求比较严格,不支持凡泛域名证书,而我恰恰用了泛域名证书。
先把证书换成最简单的独立域名证书试试。
于是,开始重新申请证书。
我的域名在godaddy托管。重新开始用acme.sh申请证书,却发现一直失败,godaddy返回出错信息。
检查了acme.sh的版本,有点过时了。
升级到最新版本,并全部重新编译系统,确保不会因为多次直接修改系统,而带来潜在问题。
然而没用,问题依旧。
百度,谷歌搜索,也不清楚原因。
最后,打开acme的文档,才发现问题所在:
godaddy从去年开始,只有满足两个条件之一,才允许使用acme来申请证书:
条件1是买了他家10个域名
条件2是缴费成为会员。
典型的店大欺客,太垃圾了:
不支持没有关系,可以理解:
免费证书显然影响了收费证书业务,又增加了网络带宽和算力的消耗
但应该在网站上明确说明,而不是支持时大肆宣传,关闭时偷偷默默。
江湖救急,在低价的ssls.com申请了一个证书,先用起来。
有一月的试用期。到时再决定是付费,还是继续换成免费的证书
音流是国人近期开发的一个音乐播放器
与Tempo(老外开发)一样,需搭配NAS或自建服务器使用。
界面简洁,支持现在主流的各种音乐服务, 包括Subsonic,Navidrome.
由于采用了跨平台的开发技术,音流有安卓手机,苹果手机,Mac OS, Windows OS各个版本
同样也支持subsonic的同步歌词
小众产品,需要到其官网下载
Tempo是开源的,也是免费的,在F-Droid中下载。
音流是闭源的,部分功能收费
都是高码率音源,带宽有要求
IPv4需要绕道香港转发,而且带宽很低,顺利播放困难较大
IPv6直连
按照协议规定,同时支持IPv4和IPv6时,自动首选走IPv6
在上海,除了东方有线,电信/联通/移动宽带都支持IPv6。如果家庭宽带连接下,播放有问题,大概率应该更换路由器了。
所谓音乐刮削,是指自动从互联网获取信息,修改音乐文件的元数据,如标题、图片、演员/歌手、歌词等
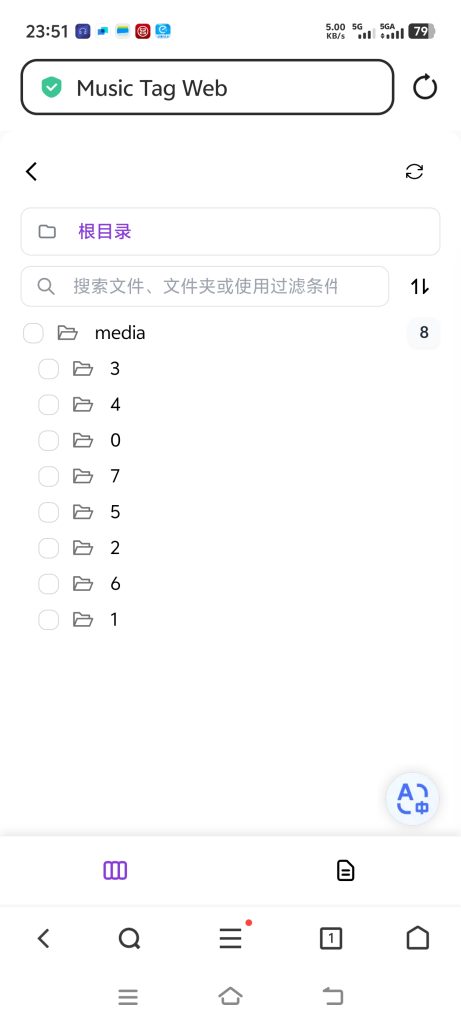
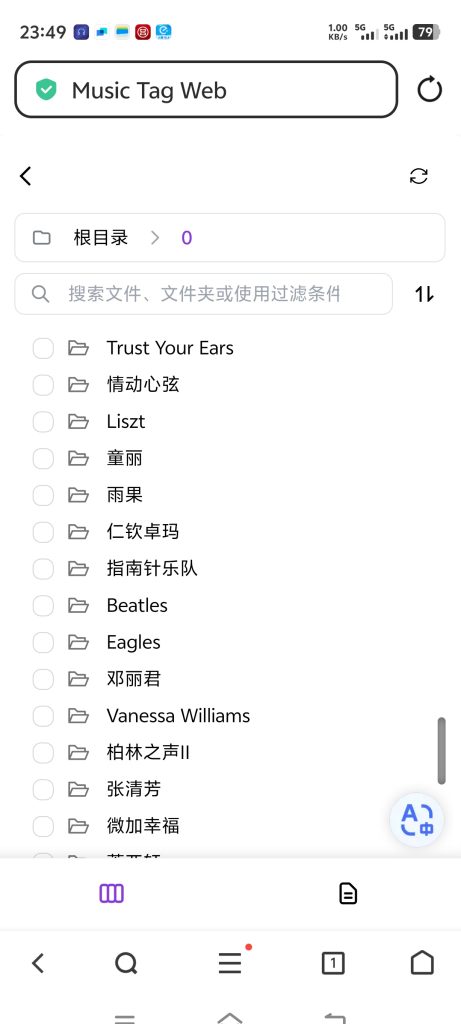
有两个流行的音乐刮削软件,MusicTag和MusicTag Web。
前者是windows 平台下的刮削软件
后者是服务器端的刮削软件,并在浏览器上操纵执行。这个软件更加方便,配置好了,可以在需要时,随时从手机中进行处理。
Docker方式安装,非常方便,但对于国内用户,由于docker hub不易访问,而国内的镜像源也于去年全部停止了,需要想其它方式来安装:
先在镜外VPS上 Pull Image 安装,并export image,再在家中的服务器或NAS上 import image。
在虚拟机上安装好MusicTag Web,并设置好对应的域名和网址后,就可以从任意的手机或PC访问了
有两个版本,V1免费,V2收费
对我而言,V1够用了
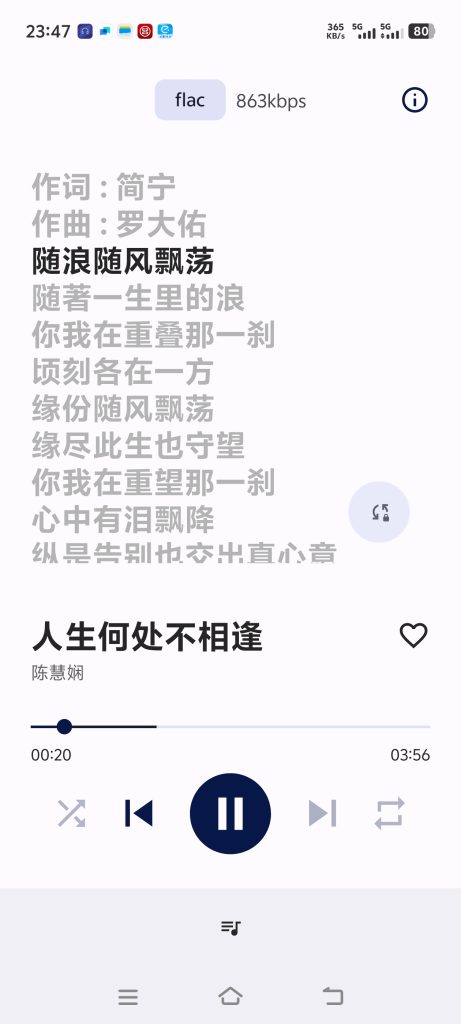
Tempo 是Android平台上,开源的Subsonic 轻量级客户端,老外开发的。
支持歌词同步显示,没有广告。
可在F-Droid 中下载。
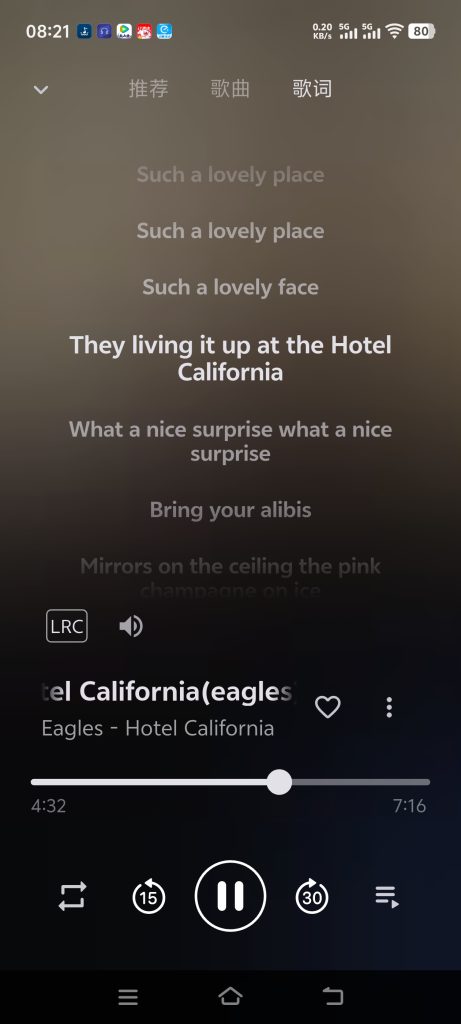
歌词显示,是Tempo apk,subsonic 客户端的一个功能,分享到其它应用,是由subsonic 服务端提供的,这里是Navidrome,不支持歌词显示
sudo apt update
sudo apt upgrade
sudo apt install apt-transport-https ca-certificates curl software-properties-common gnupg2
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo apt-key add -
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/debian $(lsb_release -cs) stable"
sudo apt update
sudo apt install docker-ce
sudo usermod -aG docker $USER
Modify footer.php:
Not display ‘Proudly powerd by…’
Modify: add line of
$utility_text = __(”)
Navidrome dosen’t support DSF/DFF decoding natively,
but it can be achieved via ffmpeg transcoding on the fly.
1 Enable transcoding in server side config file navidrome.toml:
FFmpegPath=”/opt/local/bin/ffmpeg”
EnableTranscodingConfig=”true”
2 Add flac transcode rule in Navidrome client (web browser):
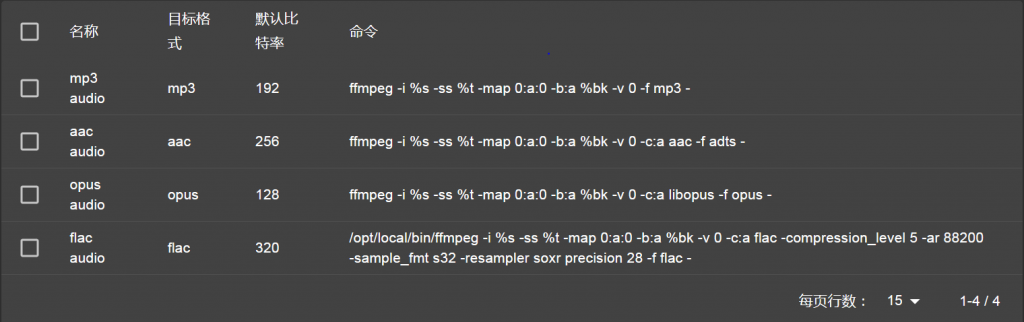
3 Select flac transcode in Tempo (Android client)